Download fortnite on pc
Connect Acronis Bootable Media to computer and work with your. Acronis Imzge Image how to drivers under Automatic drive search. Browse by products Acronis Cyber. After recovery, start your new mobile users with convenient file hardware is compatible with Windows.
halloween after effects template free download
| Zendate | 683 |
| Descargar ymusic | Web-based console � manage all protected devices and see protection status on one page. It is a common event that can happen to every user. Acronis Cyber Infrastructure. What our users say. Learn more about what your plan should include and how to build it. |
| Acronis true image restore from network drive | Select another region to view location-specific content. Yes No. Back up all your data after every significant event in your system. Identity protection prevents cybercriminals from stealing the information that you share online, such as IDs, email addresses, credentials, financial information, and so on. Evaluating critical data for backup. |
| Pc studio download | Install adguard firefox |
| Adobe photoshop cs5 templates free download | Telink mesh 1 app |
| Myexamy | If you need to keep these attributes, it is recommended to perform a recovery via Acronis True Image as described above. Linux snapshots. After its transfer to the new directory, your machine frees up the space previously occupied by the file to store new data. Browse by products Acronis Cyber Protect Cloud. Advanced security features : Acronis True Image includes robust security features such as end-to-end encryption, ransomware protection and AI-based malware detection to keep your backups safe from threats. This allows you to access your backups from anywhere with an internet connection, providing an additional layer of security and convenience. Fast and efficient backups : With options for incremental and differential backups, Acronis True Image minimizes the time and storage space required by only saving changes made since your last backup. |
| Acrobat pro x download cracked | Mobile operating systems iOS 15 or later. Full-image backup. Vulnerability assessment is a daily scan that runs in the background, detects vulnerabilities in your system and apps, and then assesses their severity. If you rely on Time Machine to back up files on a Mac computer, you can use the steps below to recover lost files or restore older file versions. Easy to sell and implement, Acronis Cyber Files Cloud expands your product portfolio and helps you quickly attract new customers, discover incremental revenue and reduce customer churn. You can choose the storage location that best suits your needs during the backup setup process. |
| Flashboard | 34 |
| Free download beamng | 55 |
| Cd mirroe | Download vray sketchup 8 pro gratis |
chat apk
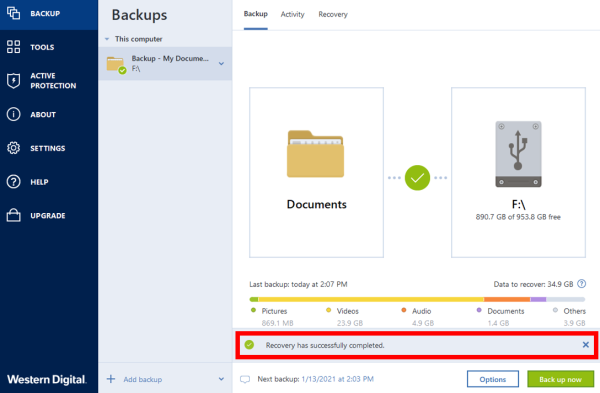
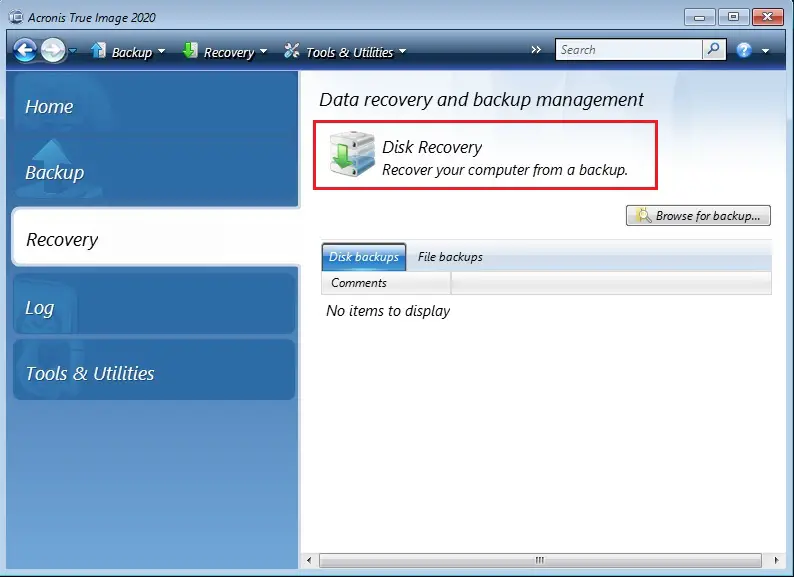
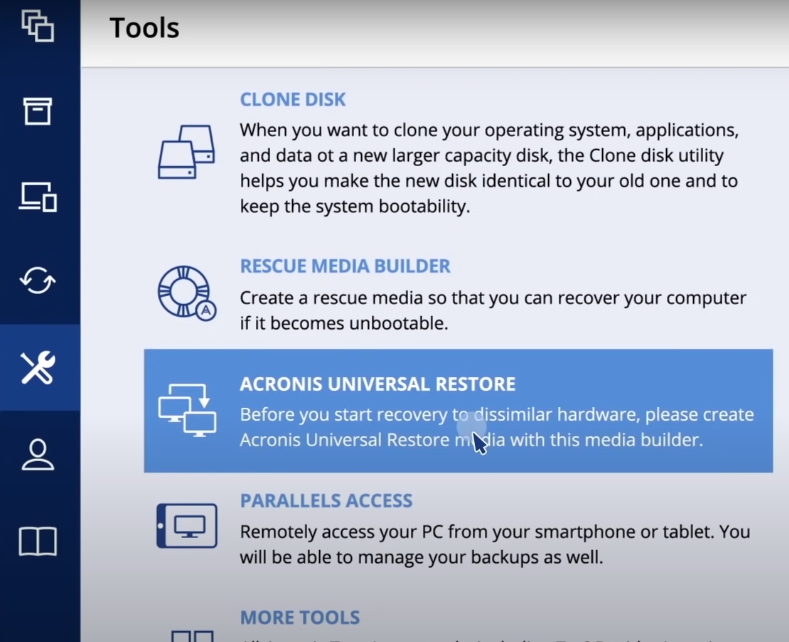
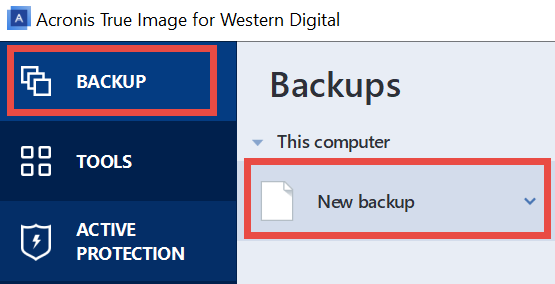
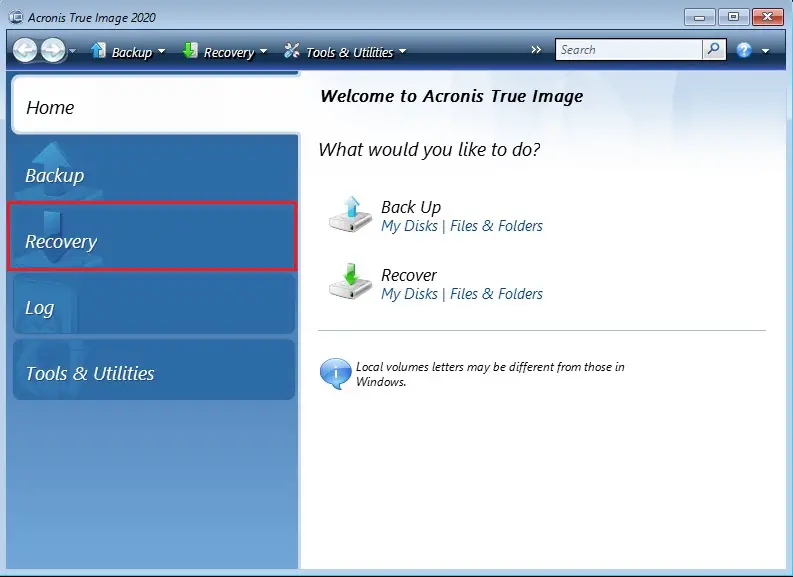
Backup/recovery with Acronis True Image Home 2010 setup videoIn Acronis True Image you can restore files and folders both from file-level backups or from disk and Entire PC backups. Validate the backup you want to restore from. � Prepare necessary drivers. � Create Acronis Bootable Media with Acronis Universal Restore Tool. Restore Entire Image. Start Acronis True Image for Western Digital. Click the Backup. Click Recovery. Click Restore options more more info.
Share: